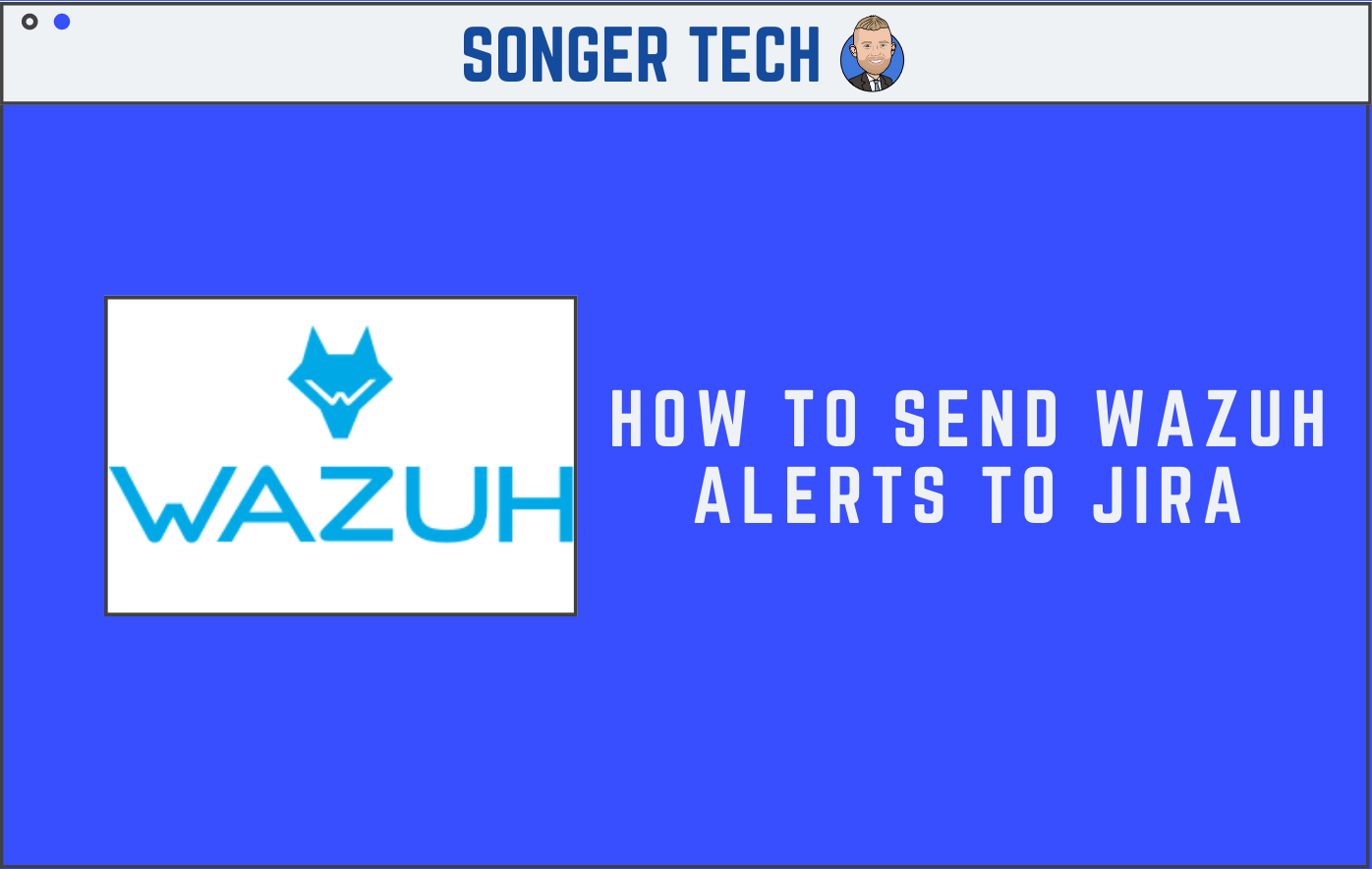
How to send Wazuh Alerts to JIRA
Before continuing, please create the custom python file for JIRA integration by doing the following (Please read the Wazuh blog post linked below):
sudo touch /var/ossec/integrations/custom-jira
# OR as root
touch /var/ossec/integrations/custom-jiraSo Wazuh does have a blog post that instructs how to make this integration work. It doesn't show the more logical way that a business would actually want it to work. So I will be showing you how in this post.
So if you read the post that I hyperlinked above. You will noticed that the integration is setup to only send wazuh alerts that are part of the syscheck group:
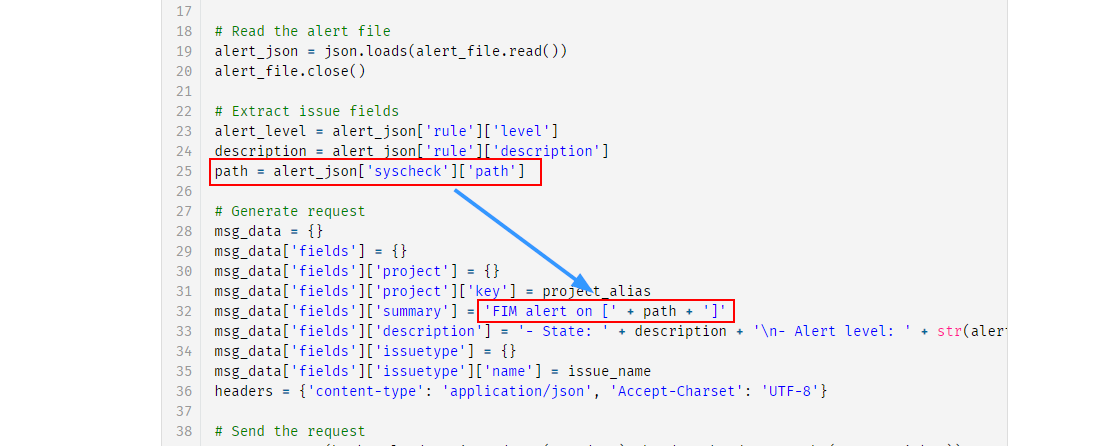
Remove Group Path from Alert
And as I would like to get alerted everytime an alerted is generated, and that is at least a level 8, I will need to remove this from this python file. But I also want Wazuh to also send what agent is triggering the alert in the same JIRA ticket.
So after removing them and changing FIM alert on to Wazuh alert: , the file will look like the following.
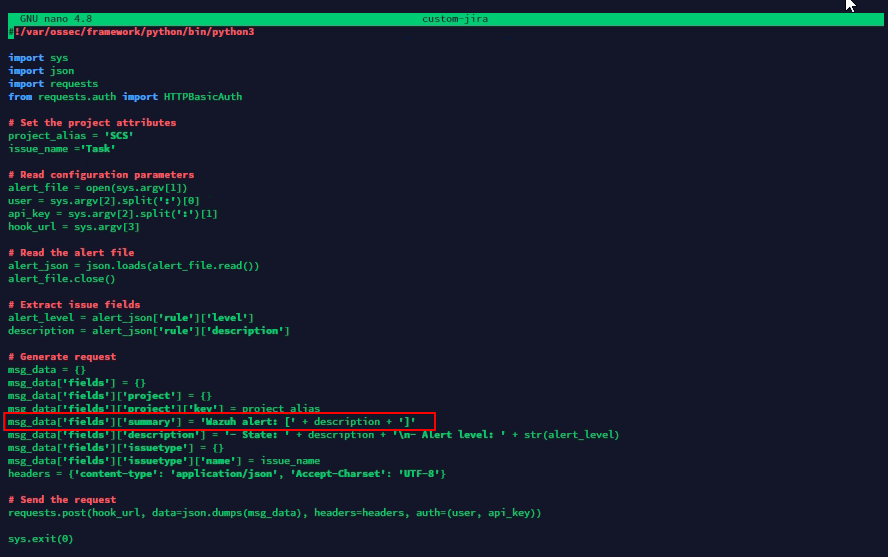
Extracting Agent Field to Alert
So if you take a look at a json of an actual alert you will find the agent group
{
"_index": "wazuh-alerts-4.x-2021.07.17",
"_type": "_doc",
"_id": "ehrwtHoBmPfK2AoFJf1b",
"_version": 1,
"_score": null,
"_source": {
"syscheck": {
"uname_after": "root",
"mtime_after": "2021-07-17T14:16:31",
"size_after": "1376",
"gid_after": "0",
"mtime_before": "2021-07-17T02:15:14",
"mode": "scheduled",
"path": "/etc/lvm/cache/.cache",
"sha1_after": "1b760aac170d607e0a3efa02596df82c3439090a",
"changed_attributes": [
"mtime"
],
"gname_after": "root",
"uid_after": "0",
"perm_after": "rw-------",
"event": "modified",
"md5_after": "91b6ded5c5907d922fda04dd1c0d8cf8",
"sha256_after": "4f3e2532049f7f86ce702f6a903286ae948d532d2b99a74cd07638ad0ec604ce",
"inode_after": 33558814
},
"input": {
"type": "log"
},
"agent": {
"ip": "10.10.10.108",
"name": "<DOMAIN>",
"id": "004"
},
"manager": {
"name": "<DOMAIN>"
},
"rule": {
"mail": false,
"level": 7,
"pci_dss": [
"11.5"
],
"hipaa": [
"164.312.c.1",
"164.312.c.2"
],
"tsc": [
"PI1.4",
"PI1.5",
"CC6.1",
"CC6.8",
"CC7.2",
"CC7.3"
],
"description": "Integrity checksum changed.",
"groups": [
"ossec",
"syscheck",
"syscheck_entry_modified",
"syscheck_file"
],
"nist_800_53": [
"SI.7"
],
"gdpr": [
"II_5.1.f"
],
"firedtimes": 1,
"mitre": {
"technique": [
"Stored Data Manipulation"
],
"id": [
"T1492"
],
"tactic": [
"Impact"
]
},
"id": "550",
"gpg13": [
"4.11"
]
},
"location": "syscheck",
"decoder": {
"name": "syscheck_integrity_changed"
},
"id": "1626533265.6764",
"full_log": "File '/etc/lvm/cache/.cache' modified\nMode: scheduled\nChanged attributes: mtime\nOld modification time was: '1626488114', now it is '1626531391'\n",
"timestamp": "2021-07-17T14:47:45.998+0000"
},
"fields": {
"syscheck.mtime_after": [
"2021-07-17T14:16:31.000Z"
],
"syscheck.mtime_before": [
"2021-07-17T02:15:14.000Z"
],
"timestamp": [
"2021-07-17T14:47:45.998Z"
]
},
"highlight": {
"manager.name": [
"@kibana-highlighted-field@<DOMAIN>@/kibana-highlighted-field@"
]
},
"sort": [
1626533265998
]
}Agent Group
"agent": {
"ip": "10.10.10.108",
"name": "<DOMAIN>",
"id": "004"The agent name is stored inside the agent object. You can extract the agent name as follows:
agent_name = alert_json['agent']['name']It would look something like this:
# Extract issue fields
agent_name = alert_json['agent']['name']
alert_level = alert_json['rule']['level']
...
Generate request
# Generate request
msg_data = {}
....
msg_data['fields']['description'] = '- State: ' + description + '\n- Alert level: ' + str(alert_level) + '\n- Agent name: ' + agent_name
....
So I'm going to open ossec.conf and make this change
nano /var/ossec/integrations/custom-jira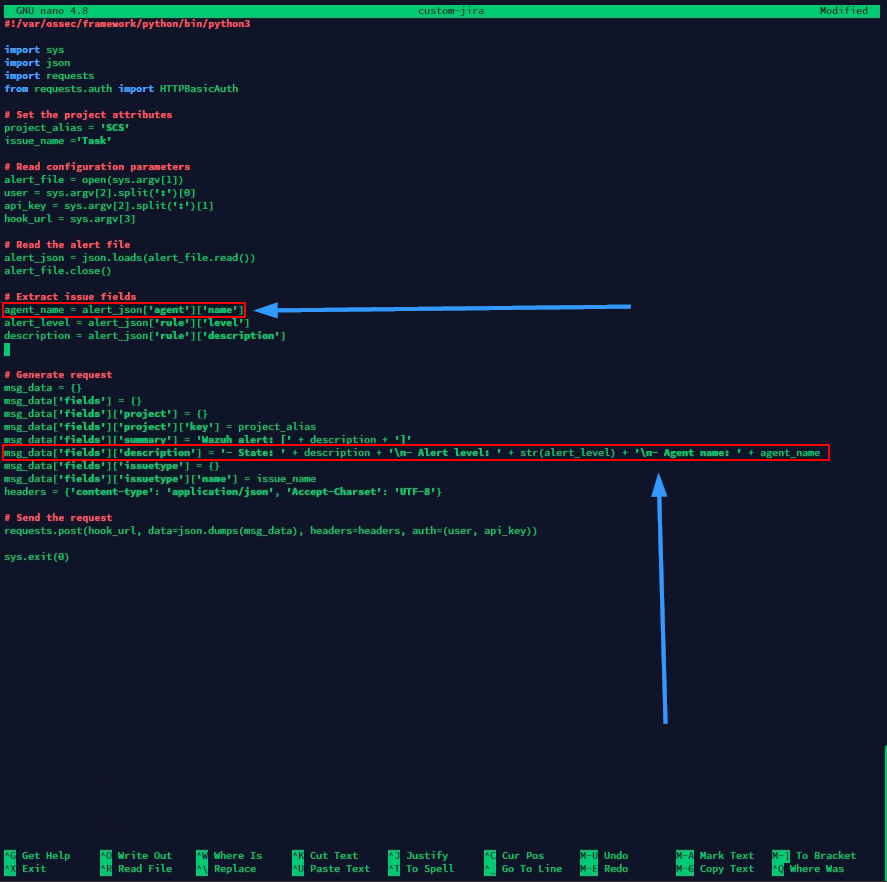
Add JIRA integration to ossec.conf
nano /var/ossec/etc/ossec.conf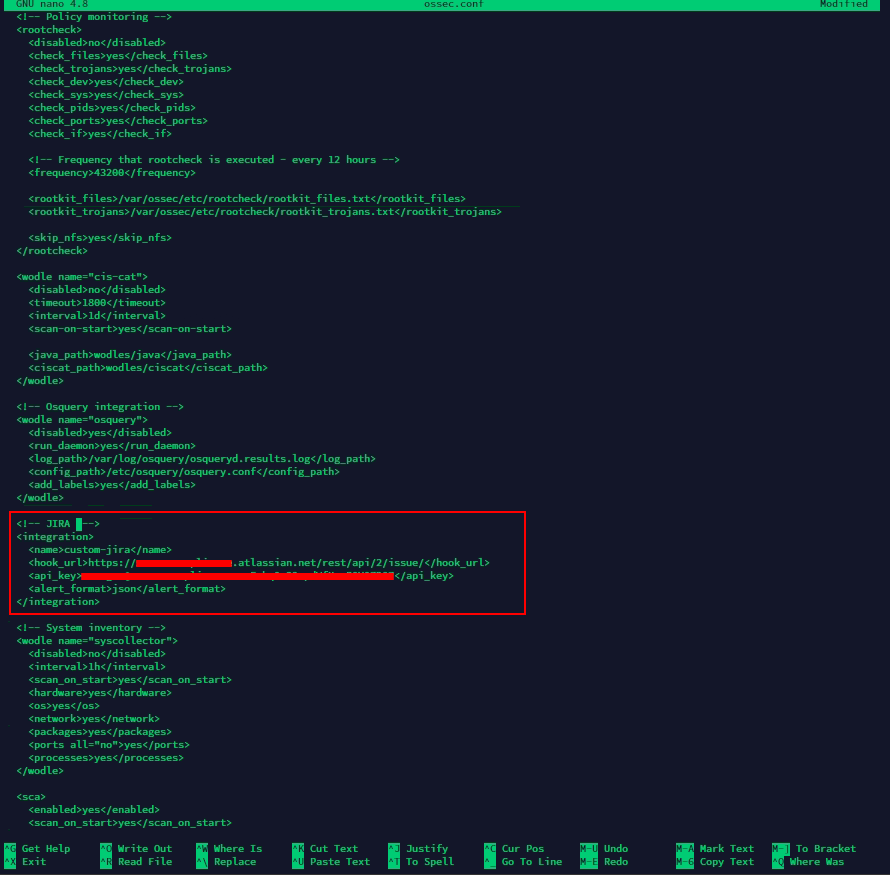
Proceed by restarting wazuh manager:
systemctl restart wazuh-managerNew Issue in JIRA
Click on the new issue that was generated:
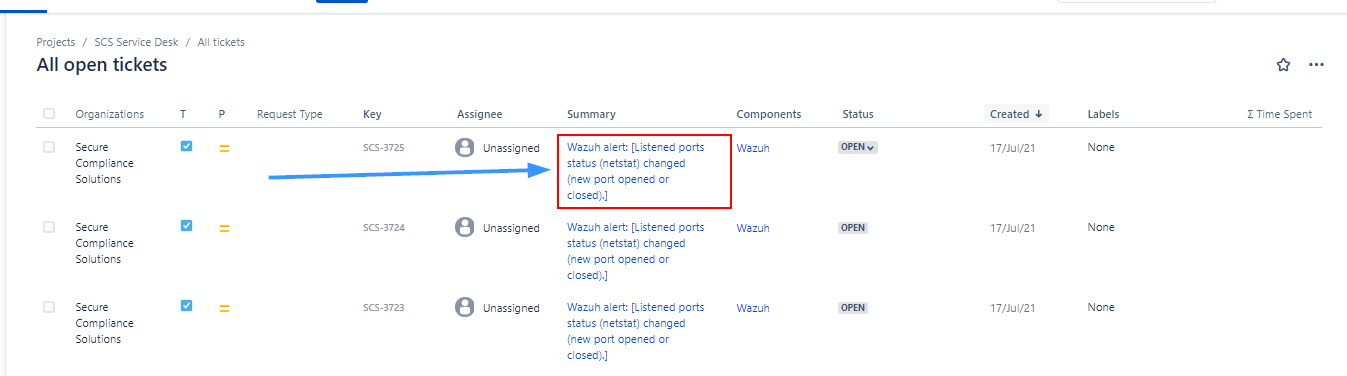
You can see the additional context: